Recently, we created a new child domain in the existing AD forest with two new Windows Server 2012 R2 domain controllers. The AD authentication and AD replication between DCs are working fine.
Today, we are trying to set up a third party app (Splunk) with the secure LDAP authentication to the child domain AD. The child domain DC servers are hardened to require signing on the LDAP server signing requirements policy.
However, we get an error “the connection reset by the peer” in the third party app’s LDAP connection test. On the DC server, there is a warning in System event - Event ID 36886 “No suitable default server credential exists on this system. …”
Troubleshooting
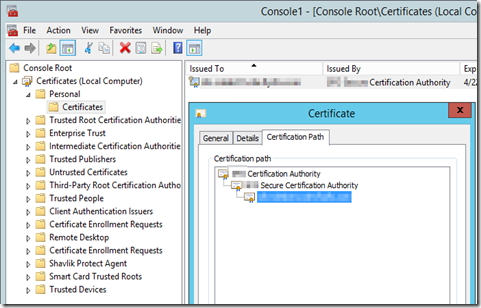
- According to MS KB321051, “The LDAPS certificate is located in the Local Computer’s Personal certificate store.”
- Open the Certificates MMC for the Local Computer on the child domain controller. There is a server cert for this domain controller.
- However, this cert is not fully trusted because the root CA cert is not trusted, which it is caused by not in the Trusted Root Certification Authorities store.
- I guess this server cert is created / issued when promoting the server to DC, and the cert is issued by the internal Windows Server 2008 enterprise intermediate CAs. (There is a Windows Server 2008 enterprise root CA and intermediate CA in the AD forest.)
- I find the root CA cert is in the Intermediate Certification Authorities store. I’m not sure why. (The enterprise root CA and intermediate CA are set up by someone else.) This is the cause of the issue.
Solution
- There are two ways to put the root CA cert back to the trusted root CA store.
- I can copy and paste the root CA cert from the intermediate cert store to the trusted root CA store.
- I download the CA certificate chain, open the root CA cert, and install it on the child DC server. Make sure specify the store location is the Local Machine and the Trusted Root Certification Authorities. The default automatic selection will place the root CA cert in the intermediate CA store again.
- Once the root CA cert is in the right store location, the child DC’s cert shows trusted. The LDAPS connection test in the third party app is successful.





Thanks for the info, Eddie. Looks like you've solved exactly my case.
ReplyDeleteEddie'S Blog: Event Id 36886 “No Suitable Default Server Credential Exists On This System” Fix >>>>> Download Now
ReplyDelete>>>>> Download Full
Eddie'S Blog: Event Id 36886 “No Suitable Default Server Credential Exists On This System” Fix >>>>> Download LINK
>>>>> Download Now
Eddie'S Blog: Event Id 36886 “No Suitable Default Server Credential Exists On This System” Fix >>>>> Download Full
>>>>> Download LINK