- Download nmap binaries. For Windows OS, download the command-line zipfile is sufficient.
- Unzip the zip file, and install Winpcap and Visual C++ Redistributable Package installer included in the zip file
- Open command prompt
- Run “nmap –sU –p53 –script=dns-recursion <DNS_Server_IP>”
- If the server allows resursion, it shows “Recursion appears to be enabled”
To prevent the DNS server from being used for DNS amplification attacks, disable DNS recursion on the public facing DNS server. The DNS recursion should be enabled on the DNS server serving the internal client.
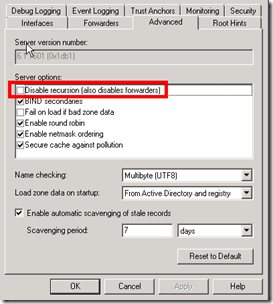
On a Windows DNS server, this can be done under the DNS server properties, Advanced tab, Server options, check the checkbox “Disable recursion (also disable forwarders)”


No comments:
Post a Comment